TLDR; Resolve the ERR_CERT_AUTHORITY_INVALID issue on browsers with https using self-signed SSL certificate by generating your own local CA (Certificate Authority) with OpenSSL on Windows/MacOS for ABAP 1909 Developer Edition.
More Info: C_TAW12_750 Key Points
I’ll share in a few simple steps, how I was able to generate my own local CA with OpenSSL and use that to sign the SSL certificate that comes delivered in ABAP 1909 Developer Edition (CN=*.dummy.nodomain) to get rid of the annoying browser warning messages when accessing any URLs served through HTTPS on this local ABAP development environment.
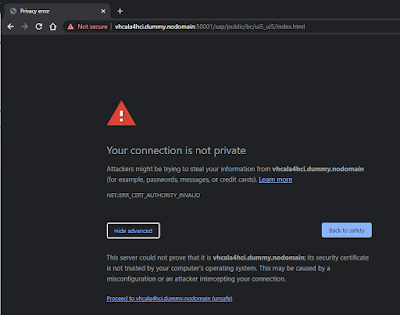
Basically, we go from this….
Annoying browser error and SSL status that says Not secure
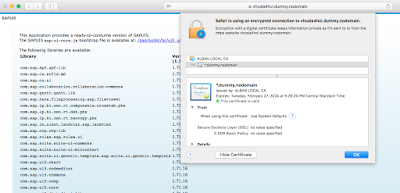
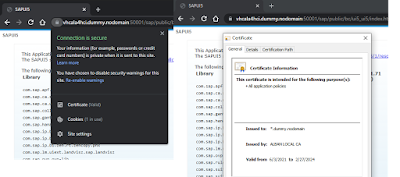
to this on Safari in MacOS or Chrome in Windows….
Ahhh…much better! A perfect, no error valid SSL on a local ABAP dev server
Introduction
The ABAP 1909 Developer Edition comes with a self-signed certificate that will technically serve “secure” HTTPS traffic for local development but browsers and even some API software/tools today frown upon self-signed certificates so much so that they labelled it as “Not secure” or just wouldn’t work with it – I am really over simplifying the reason here…
While looking around for some ideas, I came across this page on Let’s Encrypt’s website – https://letsencrypt.org/docs/certificates-for-localhost/ where it says and I quote below…
The best option: Generate your own certificate, either self-signed or signed by a local root, and trust it in your operating system’s trust store. Then use that certificate in your local web server.
So, first of all, we already have our own certificate that’s self-signed on the ABAP server – what’s missing is just
1. Generating the local root CA,
2. Trust the local root CA it in Windows / MacOS,
3. Add the local root CA into SAP using transaction STRUST
4. And then finally, use OpenSSL again to sign the SSL certificate that’s already on the ABAP server and import the certificate response back to the ABAP server.
4 simple steps – Let’s get to it!
Prerequisite – You will need OpenSSL
You can get OpenSSL for Windows here – https://slproweb.com/products/Win32OpenSSL.html and I downloaded the Win64 version for my Windows 10 machine.
For MacOS – you simply need to run the following command in your terminal.
brew install openssl
#or#
brew upgrade openssl
Step 1 – Generate Local Certificate Authority with OpenSSL
If you refer to Let’s Encrypt’s page above, it mentioned that you could use minica as a local CA to sign and issue your certificates and it would be valid for 2 years and 30 days. This feels a little overkill for my use case of just trying to sign a single SSL for the ABAP server so, I opted for a complete manual way with OpenSSL – and it only takes 2 simple command.
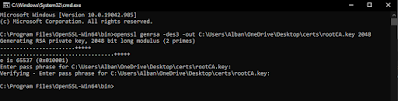
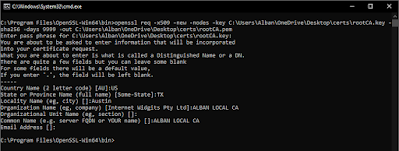
The first command is to create a private key that is 2048 bits long and this will prompt you to enter a password to create the key file. I entered something simple like ‘12345’ as the password.
openssl genrsa -des3 -out rootCA.key 2048
And with that private key generated, we will now generate the root certificate using the following command below and you will be prompted to enter the password that you’ve created for the key in the step above and also enter some basic information for the local CA.
openssl req -x509 -new -nodes -key rootCA.key -sha256 -days 9999 -out rootCA.pem
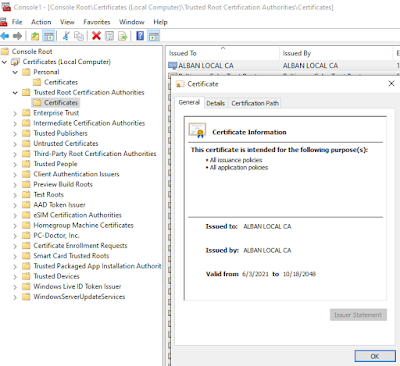
That’s it! We now have a local root CA (called ALBAN LOCAL CA – in my example above) certificate that we can now trust it in Windows / MacOS.
Step 2 – Trust the local root CA in Windows / MacOS
Here are the steps for adding the local root CA to Windows.
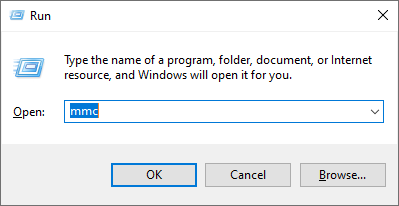
1. Click on Start and Run > mmc
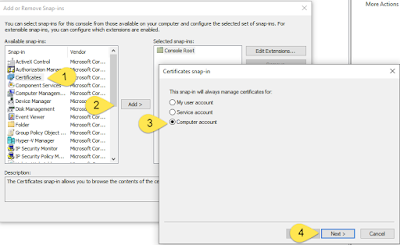
2. Click on “File” > “Add/Remove Snap-in” to add the “Certificates” Snap-in (or Ctrl + M)
3. Select manage certificates for “Computer account” and snap-in will always manage the “Local computer” in the next two prompt windows and click “Finish”
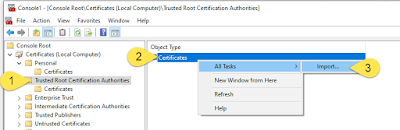
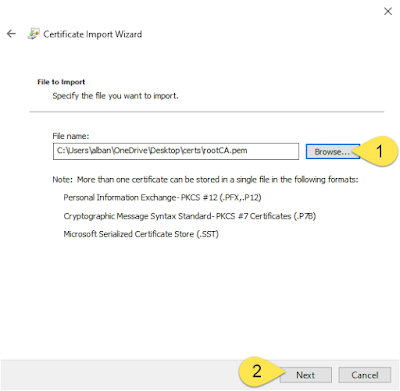
4. Double-click on “Trusted Root Certification Authorities” and in the Object Type window – Right-Click on “Certificates” > All Tasks > Import
5. Click “Next” to advance to the next window and select the local root CA certificate “rootCA.pem” file that was generated earlier.
6. Click “Next” again till you get to the end and save the certificate in “Trusted Root Certification Authorities”.
7. Repeat step 4 – 6 above but this time, import the certificate into “Personal” > “Certificates” folder.
Screen-shots for references below.
Step 2.1 (Windows)
Step 2.2 (Windows)
Step 2.3 (Windows)
Step 2.4 (Windows)
Step 2.5 (Windows)
Step 2.6 (Windows)
Here are the steps for adding the local root CA to MacOS.
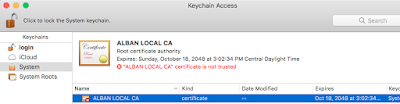
1. Run Keychain Access in Spotlight (Cmd + Space)
2. Drag and drop the “rootCA.pem” file into the “System” keychain
3. You should now see that the Certificate has been added but by default, it is still not trusted.
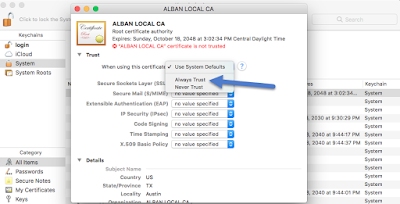
4. Double-click on the certificate and in the “Trusted” section, change the drop-down to “Always Trust”. This should then change all the other options below down to “Always Trust” as well.
5. Close the window and now, it should show that the local root CA certificate is now trusted!
Screen-shots for references below.
Step 2.1 (Mac)
Step 2.2 (Mac)
Step 2.3 (Mac)
Step 2.4 (Mac)
Step 2.5 (Mac)
Step 3 – Add the local root CA to SAP (STRUST)
Now, we head into SAP and also add the local root CA certificate in transaction STRUST. We have to first import the certificate, add it to the certificate list and then export the certificate as a Trust CA into the database table VSTRUSTCERT.
1. Double click on “SSL client SSL Client (Standard)” folder and click on “Change”
2. Import the certificate by selecting “Certificate” > “Import”
3. Browse or enter the path to the “rootCA.pem” certificate file and click on the green tick.
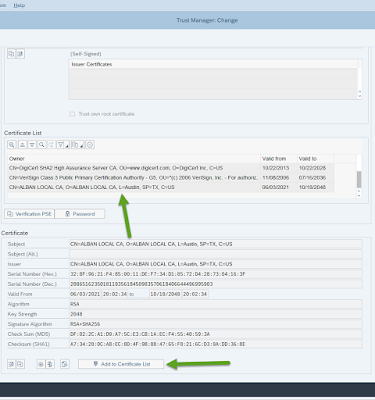
4. You should see the certificate details in the lower screen and click on the button “Add to Certificate List” (VERY IMPORTANT STEP)
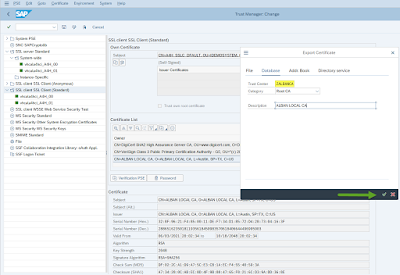
5. With the newly added local root CA certificate still selected, we now export this to the database as a Root CA by selecting “Certificate” > “Export”
6. Click over to the “Database” tab and fill in the Trust Center, select Root CA as the Category and enter a Description. Make sure to prefix the Trust Center naming with a “Z”. Click the green tick and you should get a success message that says “Certificate saved in database”. This would then create a new entry in the table VSTRUSTCERT.
Screen-shots for references below.
Step 3.1 (STRUST)
Step 3.2 (STRUST)
Step 3.2 (STRUST)
Step 3.4 (STRUST)
Step 3.5 (STRUST)
Step 3.6 (STRUST)
Step 4 – Create a Certificate Request, sign existing SSL cert in ABAP 1909 with the local root CA and import the certificate response back into ABAP 1909
This are the last few remaining steps in transaction STRUST and also one more OpenSSL command. We’re almost there… I promise.
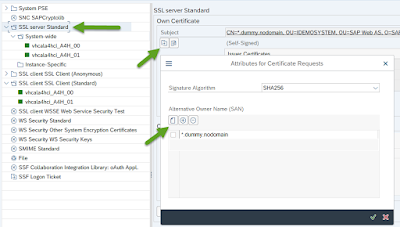
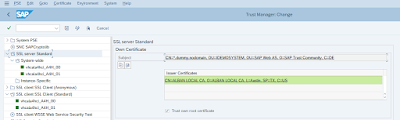
1. In STRUST – Double-click on “SSL server Standard” folder and click on the button “Create certificate request”. Here, select SHA256 as the algorithm and also enter “*.dummy.nodomain” in the Alternative Owner Name (SAN) table.
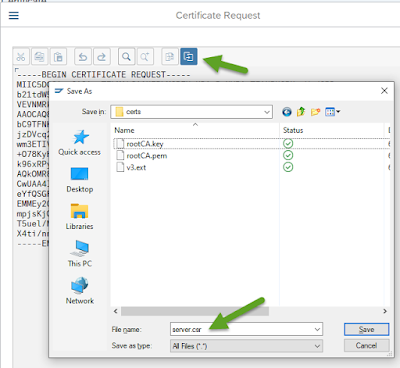
2. Save the certificate request as a local file and name it “server.csr” and save it in the same folder as the local root CA key and certificate.
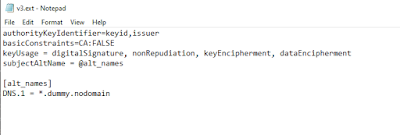
3. Now, in order to have a certificate that meets today’s SSL standard, we will need to include in the certificate the Subject Alternative Names (SAN). To do this, using Notepad, create a file called v3.ext and enter the following into the file and SAVE it.
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = *.dummy.nodomain
4. Using OpenSSL again, we run the following command to finally sign and issue a new SSL certificate (server.crt) using all the other files that we’ve generated so far. You will be prompted again for the password for the local root CA key.
openssl x509 -req -in server.csr -CA rootCA.pem -CAkey rootCA.key -CAcreateserial -out server.crt -days 999 -sha256 -extfile v3.ext
5. Last and final step – in STRUST transaction, we import the certificate response (server.crt) file back into the ABAP server.
Screen-shots for references below.
Step 4.1 (STRUST)
Step 4.2 (STRUST)
Step 4.3 (EXT file)
Step 4.4 (OpenSSL)
Step 4.5 (STRUST)
And we’re DONE! Our ABAP 1909 Developer Edition server is now capable of serving a valid HTTPS urls or OData services that browsers and other software/tools will love. Oh and you don’t even need to restart ICM because that’s already being taken care of automatically…
ICM is notified.. w00t!
Source: sap.com









No comments:
Post a Comment