In this blog, I just show how to build a simple XSS example in Java and then try to implement the same in ABAP as well.
I have a github repository where a simple Java Servlet is developed.
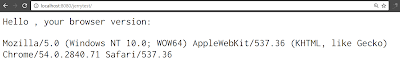
Simply clone it locally and run as Server via url: http://localhost:8080/jerrytest, and it will print out the user gent field of the current http request.
I have a github repository where a simple Java Servlet is developed.
Simply clone it locally and run as Server via url: http://localhost:8080/jerrytest, and it will print out the user gent field of the current http request.
Now append the parameter ?id=Jerry,Wang to the url, and this parameter will be echoed in the output as well.
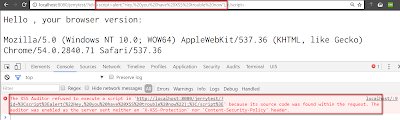
What happens if I append an executable Script tag in the parameter place?
Then I tried with this fragment below. To my surprise, I never saw the expected alert popup. The error message in Chrome development tool tells the truth.
Since I am using Tomcat as my local test server and I found from this blog Cross-site Scripting (XSS) Prevention in Apache Tomcat 7 that Cross Site Scripting protection is by default turned on.
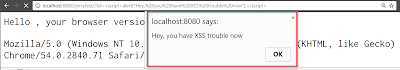
As a result in my Servlet implementation I deactivate this protection temporarily by adding a new header field to http response.
And after restart of Tomcat, I see the expected popup in the end.
And now I try to simulate the same in ABAP.
I create a new ICF node and its handler class in tcode SICF:
The implementation of this handler class simply display the passed-in parameter with name “ID”.
In normal case it works fine:
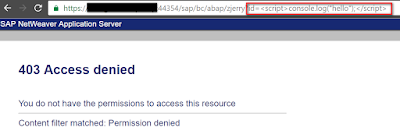
Now try XSS access:
Error message:
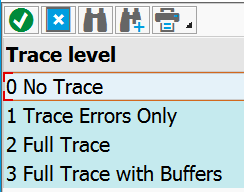
Go to tcode SMICM, set trace level to 3:
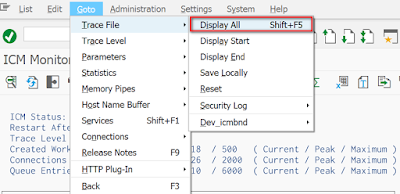
And repeat the XSS access, and then display trace file in tcode SMICM:
From trace file, I get to know the passed-in url “id=<script>console.log(“hello”);</script>” matches the filter pattern configured in ICM, so this request is filtered out and has no chance to be executed at all.
This test result just shows the fact that ABAP Netweaver acting as a Web server has its own built-in XSS protection as well.










No comments:
Post a Comment