This document shows how to configure SAP AS ABAP for authentication with x.509 client certificates. It shows the procedure used to create a simple Certification Authority (CA) using OpenSSL and how to generate client certificates from this CA.
Install the SAP Cryptographic Library. The following are minimal parameters to enable SSL
The last parameter is not necessary to enable SSL, however is required for the client authentication process which is the main topic of this document.
Configure SAP Web AS to support SSL according to these instructions from SAP Help
This is how the main SSL Server certificate PSE looks like for this example:
The server certificate (signed by SAP TCS) looks as follows (make sure to upload the SAP Server CA root certificate to your browser to ensure the certificate chain is complete):
Enabling SSL
Install the SAP Cryptographic Library. The following are minimal parameters to enable SSL
- ssl\ssl_lib = S:\usr\sap\K20\SYS\exe\run\sapcrypto.dll
- sec\libsapsecu = S:\usr\sap\K20\SYS\exe\run\sapcrypto.dll
- sec\ssfapi_lib = S:\usr\sap\K20\SYS\exe\run\sapcrypto.dll
- ssf\name = SAPSECULIB
- icm\server_port_1 = PROT=HTTPS, PROT=1443, TIMEOUT=900
- icm/HTTPS/verify_client = 1
The last parameter is not necessary to enable SSL, however is required for the client authentication process which is the main topic of this document.
Configure SAP Web AS to support SSL according to these instructions from SAP Help
This is how the main SSL Server certificate PSE looks like for this example:
The server certificate (signed by SAP TCS) looks as follows (make sure to upload the SAP Server CA root certificate to your browser to ensure the certificate chain is complete):
Test SSL using the info URL of ICM
Creating x.509 credentials
This section shows how OpenSSL was used to setup a CA and create user credentials. It assumes OpenSSL package is installed on a Linux system.
Preparations
These are instructions to configure OpenSSL to create a root Certificate Authority (CA)
# Set up the relevant directories
mkdir -p /etc/ssl
mkdir -p /etc/ssl/private
chmod og-rwx /etc/ssl/private
mkdir -p /etc/ssl/certs
mkdir -p /etc/ssl/crl
mkdir -p /etc/ssl/newcerts
Create a configuration file for OpenSSL (see Appendix A)
# Set up the location of your OpenSSL configuration file
export OPENSSL_CONF=”/etc/ssl/openssl.cnf”
# Create the random file
openssl rand -out /etc/ssl/private/.rand 1024
chmod og-rwx /etc/ssl/private/.rand
Create the Root CA
# Create an RSA private key
openssl genrsa -des3 -out /etc/ssl/private/myrootca.key 2048
chmod og-rwx /etc/ssl/private/myrootca.key
# Fill in the certificate request
openssl req -new -key /etc/ssl/private/myrootca.key -out /tmp/myrootca.req
# Sign its own certificate request
openssl x509 -req -days 7305 -sha1 \
-extfile /etc/ssl/openssl.cnf -extensions v3_ca \
-signkey /etc/ssl/private/myrootca.key \
-in /tmp/myrootca.req -out /etc/ssl/certs/myrootca.crt
# Delete the certificate request
rm -f /tmp/myrootca.req
Import this Root CA into your Internet browser. This root CA will be the signer of user credentials, in order to complete the certification path it is necessary to load this certificate into the trusted root CA container of the Internet browser.
Create user credentials
A Linux system (e.g.,Fedora 9) was used in this example to create user credentials
Login to Linux (as a regular user) and create the following directories
$HOME/.ssl/cers
$HOME/.ssl/private
chmod og-rwx $HOME/.ssl/private
# Create an RSA private key
openssl genrsa -des3 -out ~noe/.ssl/noe.key 2048
chmod og-rwx ~noe/.ssl/private/noe.key
# Fill in the certificate request
openssl req -new -key ~noe/.ssl/private/noe.key -out /tmp/noe.req
Now login as root and sign the user certificate request using the Root CA certificate
# Sign the certificate request
openssl x509 –req –days 3650 –extensions v3_req \
-CA /etc/ssl/certs/myrootca.crt –Cakey /etc/ssl/private/myrootca.key \
-CAserial /etc/ssl/myrootca.srl –Cacreateserial \
-in /tmp/noe.req –out ~noe/.ssl/certs/noe.crt
In order to upload the user credentials to Internet Explorer, for example, the certificate needs to be exported to format PKCS#12.
Login or return to the regular Linux user session
# Export user certificate as PKCS#12
openssl pkcs12 –export –in ~noe/.ssl/certs/noe.crt –inkey ~noe/.ssl/private/noe.key –out ~noe/.ssl/certs/noe.p12
Transfer file “noe.p12” to your PC for upload to Internet Explorer.
Make sure this certificate is imported into the personal container
SAP configuration
Load the Root CA certificate into the SSL Server PSE, use transaction STRUST
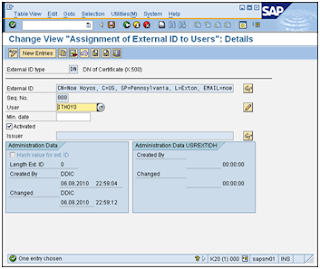
Create a mapping between the user credentials and the ABAP user ID in table USREXTID. Use transaction SM30 and view VUSREXTID; use external ID type “DN”.
Make sure the External ID matches exactly (spaces count) with the Subject of the user credentials certificate
Make sure the entry is marked as active.
Restart ICM using transaction SMICM
IE will present a list of user certificates suitable for login, select the appropriate credentials and choose OK
You will be logged in without being asked for a password
Effects of parameter Icm/HTTPS/verify_client
Parameter Icm/HTTPS/verify_client controls whether a client certificate is just requested (1) or required (2). A value of 1 will cause the authentication to fall back to another method, for example user and password. On the other hand, a value of 2 will not allow any other authentication methods and failure to present a client certificate will terminate the session immediately.
Appendix A: OpenSSL configuration file
#
# OpenSSL configuration file.
#
# Establish working directory.
dir = /etc/ssl
[ ca ]
default_ca = CA_default
[ CA_default ]
serial = $dir/serial
database = $dir/certindex.txt
new_certs_dir = $dir/certs
certificate = $dir/cacert.pem
private_key = $dir/private/cakey.pem
default_days = 365
default_md = md5
preserve = no
email_in_dn = no
nameopt = default_ca
certopt = default_ca
policy = policy_match
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ req ]
default_bits = 1024 # Size of keys
default_keyfile = key.pem # name of generated keys
default_md = md5 # message digest algorithm
string_mask = nombstr # permitted characters
distinguished_name = req_distinguished_name
req_extensions = v3_req
[ req_distinguished_name ]
# Variable name Prompt string
#————————- ———————————-
0.organizationName = Organization Name (company)
organizationalUnitName = Organizational Unit Name (department, division)
emailAddress = Email Address
emailAddress_max = 40
localityName = Locality Name (city, district)
stateOrProvinceName = State or Province Name (full name)
countryName = Country Name (2 letter code)
countryName_min = 2
countryName_max = 2
commonName = Common Name (hostname, IP, or your name)
commonName_max = 64
# Default values for the above, for consistency and less typing.
# Variable name Value
#———————— ——————————
0.organizationName_default = My Company
localityName_default = My Town
stateOrProvinceName_default = State or Providence
countryName_default = US
[ v3_ca ]
basicConstraints = CA:TRUE
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer:always
[ v3_req ]
basicConstraints = CA:FALSE
subjectKeyIdentifier = hash











No comments:
Post a Comment