Recently I was assigned to a prototype development which needs to consume ILM framework in ABAP on-Premise system. I have divided the whole ILM topic into two separate blogs. The first one which we are going to discuss in this blog is to have the ability to automatically detect and destruct destroyable data (and its related component). Destroyable data is defined as data that are expired or no more needed based on pre-defined customizable business scenario. One such business scenario could be “retention period”.
one simple answer would be to remove the unnecessary data and lessen the load on our application and DB.
It’s important to mention it could be achieved without ILM framework, however advantage of using ILM framework can’t be ignored more so where time and less complexity is directly related to Total cost of Development.
Advantages:
1. Auto-enabled Application logging
2. Least amount of coding
3. Customizable business scenarios for deciding the destroyable data
Pre-requisite
1. ILM business function must be switched on : First thing first, you need to ensure ILM business function is switched on. For various reason is some organization it is not switched on. Check with system administrator first.
2. Check ILM Business Function : To check if ILM is switched on or off. Go to transaction SFW5. Find ILM and you can see if its witched on or off.
Why?
one simple answer would be to remove the unnecessary data and lessen the load on our application and DB.
It’s important to mention it could be achieved without ILM framework, however advantage of using ILM framework can’t be ignored more so where time and less complexity is directly related to Total cost of Development.
Advantages:
1. Auto-enabled Application logging
2. Least amount of coding
3. Customizable business scenarios for deciding the destroyable data
How?
Pre-requisite
1. ILM business function must be switched on : First thing first, you need to ensure ILM business function is switched on. For various reason is some organization it is not switched on. Check with system administrator first.
2. Check ILM Business Function : To check if ILM is switched on or off. Go to transaction SFW5. Find ILM and you can see if its witched on or off.
Implementation Steps
Following are the main points that we will be covering in detail
1. Set configuration to define the destroyable data.
2. Create a custom delete API that perform data and its component
3. Embed the API into ILM based destruction program
Implementation Details
1. Create a destruction program in SE38 namely SAM_ILM_DES. no coding yet just we need to create a program. you can name anything starting with z or y or your namespace.
2. Configuration for ILM framework:
◈ DOBJ configuration: Enter transaction DOBJ in command box. Create a new entry. Give any destruction object name associate your destruction program name (created above) with this destruction object.
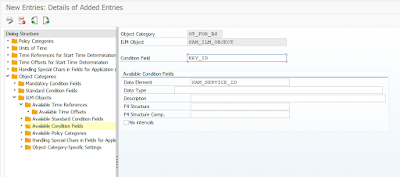
◈ IRM_CUST – Here we create one ILM object and assign above created destruction object to this ILM object.
Double click on ILM Objects
press “NEW ENTRIES” and here enter you ILM Object Name
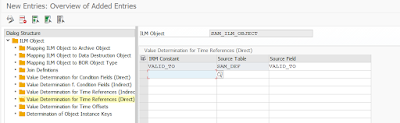
Define Available Time Reference fields which can be mapped to any time reference fields of your application table to be used for calculation of retention logic.
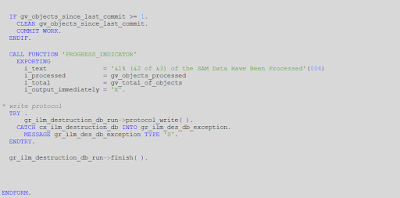
3. ILM Program: Coding Embedding delete API into ILM framework backed program as shown below
◈ Add INCLUDE destroy_prg_standard before INITIALIZATION
◈ Under INTIALIZATION add PERFORM standard_texts_init.
◈ In START OF SELECTION event, a subroutine PERFORM main.
◈ Inside main, we need to add four subroutines that are mentioned below.
◈ All above steps can be seen in above screenshot of the program
Inside routine “main”, we will have following sub routines.
◈ PREPROCESSING
◈ FILL_WORKLIST – Here we can retrieve the data from main table from which is to be scope of data destruction. Let’s say GT_WORK_LIST
◈ PROCESSING
4. You can now run this program in foreground
5. Or you can schedule this program in background and it will check the data everyday which all data has expired and will delete it

















Nice blog very useful information I will visit again to read more your post.
ReplyDeleteSecure Data Destruction