In this blog I want to explain about how to unlock the users password when it is locked using OData and Resetting the users password by giving temporary password which is been sending through mail.
Step 1. Go to t-code SEGW to create service.
Step 1. Go to t-code SEGW to create service.
Step 2. Create an entity type by giving the name as user details.
Step 3. Now provide the properties.
Step 4. Now get entity set is automatically created.
Step 5. Now we have to implement the code by redefining the methods get entity in DPC_EXT class.
Now right click on get entity and Choose Redefine.
In our scenario we have redefined get_entity and update_entity methods as shown below.
Step 6. And we have to write the code in the Re-defined method .
Based on the login user to get the user details using get entity method.
method USERDETAILSSET_GET_ENTITY.
DATA: is_key_tab TYPE /IWBEP/s_MGW_NAME_VALUE_PAIR.
READ TABLE it_key_tab INTO is_key_tab INDEX 1.
DATA(lv) = is_key_tab-value.
TRANSLATE lv TO UPPER CASE.
SELECT SINGLE Bname
Langu
FROM usr01 INTO CORRESPONDING FIELDS OF ER_ENTITY WHERE Bname = lv."is_key_tab-VALUE.
endmethod.
Step 7. After getting the user details we have to update the user password using update entity.
METHOD userdetailsset_update_entity.
DATA:is_update TYPE zcl_zuser_unlock_mpc=>ts_userdetails.
io_data_provider->read_entry_data( IMPORTING es_data = is_update ).
DATA(lv_user) = is_update-bname.
DATA:logondata TYPE uslogond.
DATA(repid) = sy-repid.
DATA(reptitle) = sy-title.
CALL FUNCTION 'SUSR_USER_LOGONDATA_GET'
EXPORTING
user_name = lv_user
IMPORTING
user_logondata = logondata
EXCEPTIONS
user_name_not_exist = 1
OTHERS = 2.
Step 8. Logic to generate a random password
DATA: lv_password(8),
lv_newpassword TYPE xu400-newcode.
DATA:lc_alphanum TYPE c.
CALL FUNCTION 'RSEC_GENERATE_PASSWORD'
EXPORTING
alphabet = lc_alphanum
output_length = 8
IMPORTING
output = lv_password
EXCEPTIONS
some_error = 1
OTHERS = 2.
Step 9. Now we have to assign a password to the user .
IF lv_password IS NOT INITIAL.
** If no number in password, insert a number to meet security policy
IF lv_password NA '123456789'.
lv_password+7(1) = '5'.
ENDIF.
lv_newpassword = lv_password.
CALL FUNCTION 'SUSR_USER_PASSWORD_PUT'
EXPORTING
user_name = lv_user
password = lv_newpassword
EXCEPTIONS
user_name_not_exist = 1
password_not_allowed = 2
OTHERS = 3.
IF sy-subrc = 0.
CALL FUNCTION 'SUSR_USER_BUFFERS_TO_DB'
EXPORTING
message_out = 'X' " note 173081
EXCEPTIONS
no_logondata_for_new_user = 1
no_init_password = 2
db_insert_usr02_failed = 3
db_update_usr02_failed = 4
db_insert_usr01_failed = 5
db_update_usr01_failed = 6
db_insert_usr05_failed = 7
db_update_usr05_failed = 8
db_insert_usr21_failed = 9
db_update_usr21_failed = 10.
IF sy-subrc <> 0.
ENDIF.
MESSAGE 'Generated password has been copied to clipboard!' TYPE 'S'.
COMMIT WORK.
DATA:wa_address TYPE bapiaddr3,
it_returns TYPE bapiret2_t,
it_email TYPE STANDARD TABLE OF bapiadsmtp,
lo_container TYPE REF TO /iwbep/if_message_container.
CALL FUNCTION 'BAPI_USER_GET_DETAIL'
EXPORTING
username = lv_user
* CACHE_RESULTS = 'X'
IMPORTING
address = wa_address
TABLES
addsmtp = it_email
return = it_returns.
IF it_email IS NOT INITIAL.
READ TABLE it_email ASSIGNING FIELD-SYMBOL(<fs_email>) INDEX 1.
DATA(v_email) = <fs_email>-e_mail.
ENDIF.
DATA: wa_docdata TYPE sodocchgi1,
wa_objpack TYPE sopcklsti1,
it_objpack TYPE TABLE OF sopcklsti1,
wa_objtxt TYPE solisti1,
it_objtxt TYPE TABLE OF solisti1,
wa_reclist TYPE somlreci1,
it_reclist TYPE TABLE OF somlreci1,
it_lines TYPE TABLE OF tline,
lv_link(35) TYPE c VALUE 'www.thesummitgroup.net',
tab_lines TYPE i,
ls_returns TYPE bapiret2.
DATA: lt_tvarcv_config TYPE TABLE OF tvarvc,
ls_tvarcv_config TYPE tvarvc,
lv_launchpad_url TYPE string,
lv_supinfo_url TYPE string.
CONSTANTS: c_htm TYPE char3 VALUE 'HTM',
c_u TYPE c VALUE 'U',
c_x TYPE c VALUE 'X',
c_space TYPE c VALUE ' ',
c_e TYPE c VALUE 'E',
c_pw TYPE char5 VALUE '{PWD}'.
IF sy-subrc = 0.
CALL FUNCTION 'READ_TEXT'
EXPORTING
client = sy-mandt
id = 'ST'
language = sy-langu
name = 'ZSRM_PWD_UNLOCK'
object = 'TEXT'
TABLES
lines = it_lines
EXCEPTIONS
id = 1
language = 2
name = 3
not_found = 4
object = 5
reference_check = 6
wrong_access_to_archive = 7
OTHERS = 8.
IF sy-subrc <> 0.
ENDIF.
LOOP AT it_lines INTO DATA(wa_lines).
APPEND wa_lines-tdline TO it_objtxt.
ENDLOOP.
REPLACE ALL OCCURRENCES OF c_pw IN TABLE
it_objtxt WITH lv_newpassword IN CHARACTER MODE.
DESCRIBE TABLE it_objtxt LINES tab_lines.
READ TABLE it_objtxt INTO wa_objtxt INDEX tab_lines.
wa_docdata-obj_name = text-020. "'TEST_HTML'.
wa_docdata-obj_descr = text-031. "'HISD - Password has been reset and your new password'.
wa_docdata-doc_size = ( tab_lines - 1 ) * 255 + strlen( wa_objtxt ).
CLEAR wa_objpack-transf_bin.
wa_objpack-head_start = 1.
wa_objpack-head_num = 0.
wa_objpack-body_start = 1.
wa_objpack-body_num = tab_lines.
wa_objpack-doc_type = c_htm.
APPEND wa_objpack TO it_objpack.
wa_reclist-receiver = v_email .
wa_reclist-rec_type = c_u.
APPEND wa_reclist TO it_reclist.
Step 10. Logic to send an email to user with new password.
CALL FUNCTION 'SO_DOCUMENT_SEND_API1'
EXPORTING
document_data = wa_docdata
put_in_outbox = c_space
commit_work = c_x
TABLES
packing_list = it_objpack
contents_txt = it_objtxt
receivers = it_reclist
EXCEPTIONS
too_many_receivers = 1
document_not_sent = 2
document_type_not_exist = 3
operation_no_authorization = 4
parameter_error = 5
x_error = 6
enqueue_error = 7
OTHERS = 8.
IF sy-subrc <> 0.
CALL FUNCTION 'BAPI_MESSAGE_GETDETAIL'
EXPORTING
id = sy-msgid
number = sy-msgno
textformat = c_htm
message_v1 = sy-msgv1
message_v2 = sy-msgv2
message_v3 = sy-msgv3
message_v4 = sy-msgv4
IMPORTING
message = ls_returns-message.
IF ls_returns-message IS INITIAL.
ls_returns-message = text-022. "'Failed to Send an Email to Supplier'.
ENDIF.
ENDIF.
ENDIF.
ENDIF.
ELSE.
lo_container = me->mo_context->get_message_container( ).
CALL METHOD lo_container->add_message_text_only
EXPORTING
iv_msg_type = /iwbep/if_message_container=>gcs_message_type-error
iv_msg_text = 'Order Number not Valid! Do you require pass through codes to get out of line?'
iv_error_category = /iwbep/if_message_container=>gcs_error_category-processing
iv_is_leading_message = abap_true
iv_add_to_response_header = abap_true.
ENDIF.
ENDMETHOD.
Step 11. we have successfully done with coding part, now we have to execute the service.
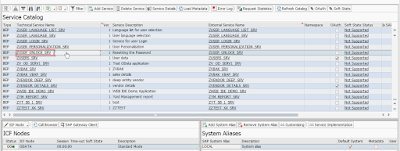
Step 12. Go to the t-code /n/IWFND/MAINT_SERVICE and click on enter.
Step 13. Now enter your project name and click on enter .
Step 14. Now we have to load the metadata by pressing the load metadata button and click on sap gateway client.
Step 15. It will navigate to execution phase of Request Uri.
Step 16. Now double click on Entity sets button and it will give pop-up like as shown below.
Step 17. Double click on the entity set name and the service url is as shown below.
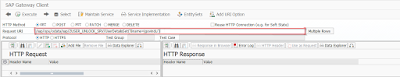
specify the particular user to reset the password in the url as shown below.
Step 18. Now click on Execute button the output can be displayed as shown below.
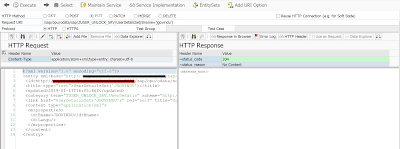
And click on Use as request the data is displayed in left side and choose radio button as put.
Simply execute status will be 204.
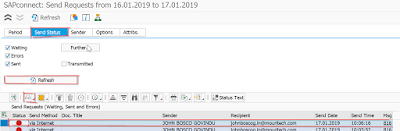
Step 19. Now the temporary password is been sent to the mail .
Go to SOST t-code there we can check the temporary password as shown below.
Step 20. Choose the send status and click on display button then the following screen we can see.
Step 21. Now user can copy this password and Re-Login using SAP GUI as shown below.
Step 22. Now user can create new password as shown below.











No comments:
Post a Comment